The jeffpc Amateur Radio Fox
There is already a number of different fox hunting designs out there—both commercial and hobbyist built. Therefore there is no practical reason to make another design, but educational and entertainment reasons are valid as well.
So I made one.
I put together a project page which talks about the project a little bit but mostly serves to point at the source, binary files, schematic, and a manual. Since it doesn’t make sense for me to repeat myself, just go over to the project page and read more about it there ;)
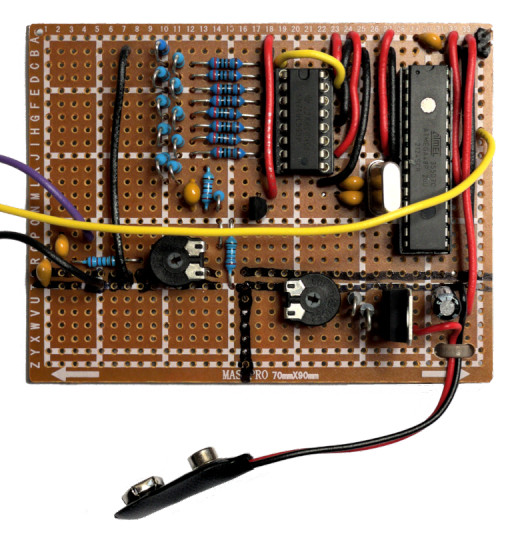
Finally, this is what the finished circuit looks like:
As always, comments, suggestions, and other feedback is welcome.
 PACELC theorem
PACELC theorem